In the landscape of cybersecurity, SMS-based multi-factor authentication (MFA) is a common security measure, but its effectiveness is increasingly being questioned. While it adds an extra layer of defense, relying solely on SMS for authentication can expose users to significant risks. Recent studies and incidents have highlighted vulnerabilities that could potentially compromise the supposed safety net this method provides.
We understand that using SMS Authentication is easy to set up and that it suits users who have a mobile phone, as it requires little setup and easy adoption by end-users. However, despite these benefits, we must tell you that this is not a secure method of secondary authentication, and you should not allow it in your organization! SMS messages rely on security of telephony networks and companies and sadly, both can be easily accessed and intercepted.
This high risk was highlighted by a recent incident where attackers got customers' VoIP and SMS logs for MFA verification messages in a cyberattack on Cisco DUO's third-party telephony provider. You may wonder, how can this happen? The way it occurs is easier than you may think. Essentially, a threat actor obtained one of the employee’s sensitive credentials of the third-party telephony company through a phishing attack, and then leveraged those credentials to get into the telephony provider's systems. Now that we have your attention, let me clarify some other basic reasons why SMS MFA Authentication is bad:
LACK OF ENCRYPTION
SMS messages are not encrypted, and as a result, they can be intercepted and read by attackers.
SOCIAL ENGINEERING
In the case of SMS-based MFA, attackers can contact the victim’s mobile service provider and impersonate the victim to obtain the SIM card information associated with the victim’s phone number. With that information, the attacker can receive SMS messages intended for the victim, bypassing the MFA process, and gaining access to the targeted account.
SIM-SWAPPING
SIM-swapping is a technique used by attackers to take control of a victim’s phone number. Attackers can impersonate the victim to convince the mobile service provider to transfer the victim’s phone number to a SIM card in their possession. With control over the victim’s phone number, the attacker gains access to the 2nd factor, an SMS code, and gains access to the targeted account with the exposed, reused, or cracked account password.
How to Minimize this Risk
If you are an existing Microsoft 365 customer and leveraging multi-factor authentication as part of your Microsoft 365 tenant, the steps below will help you strengthen your security posture when it comes to multi-factor authentication methods. If you are still leveraging third-party identity and authentication providers like Cisco DUO, this would be the right time to consider if your investments are justified and aligned with your security objectives.
Review your Legacy MFA Policies
Prior to the existence of Conditional Access Policies, MFA was enabled/enforced on a per-user basis. These are what are known as the Legacy Policies.
You can view them here.
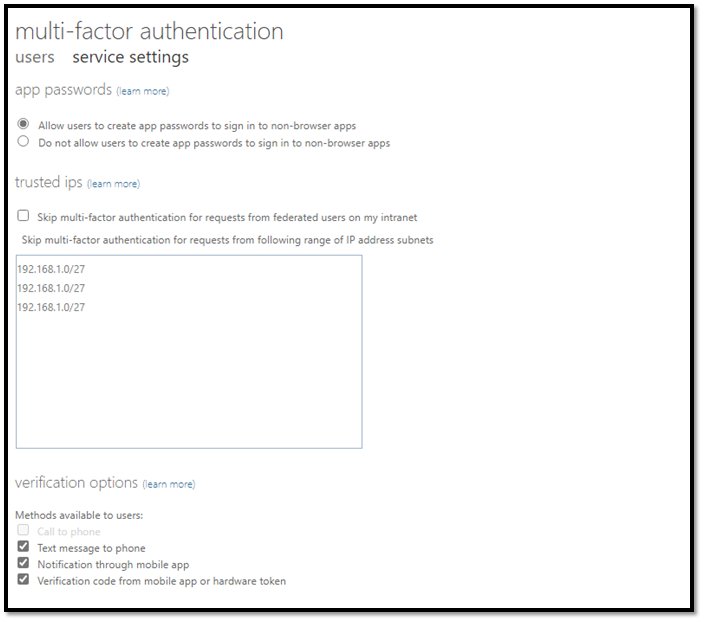
As you can see, under the ‘Methods available to users’ settings, “Text message to Phone”, “Notification through mobile app”, and “Verification code from app or hardware token” are allowed. Before these are turned off, take note of these authentication methods and cross-compare to users authentication methods to make sure they are not actively being utilized.
Review Your Password Reset Methods
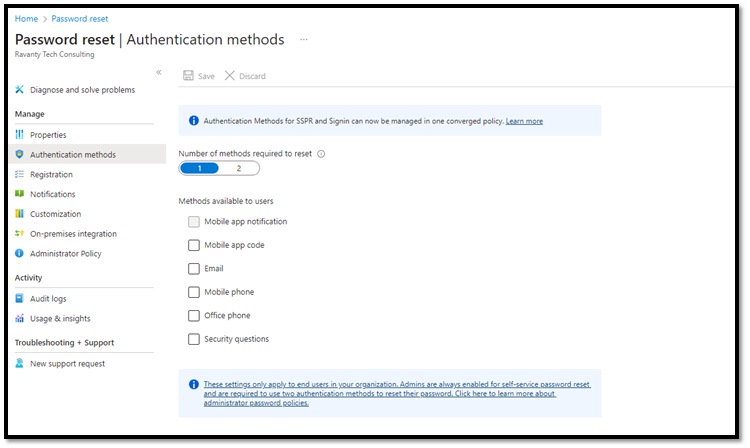
Next, you will want to head over to the Password Reset settings and look at the available methods. As you can see below, these are very unsecure methods of initiating password reset, including SMS and you want to make sure all of these are disallowed.
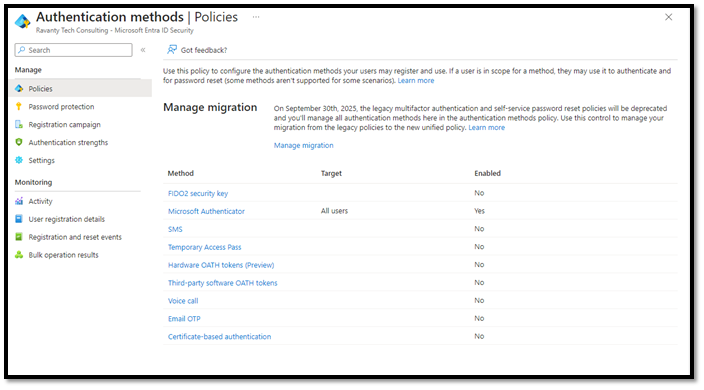
Review Authentication Methods
Authentication methods - Microsoft Entra admin center
As you can see, “Microsoft Authenticator” is enabled for “All users”.
As an added layer of protection, you will also want to head over to the “Configure” tab to review all the options with the Microsoft Authenticator.
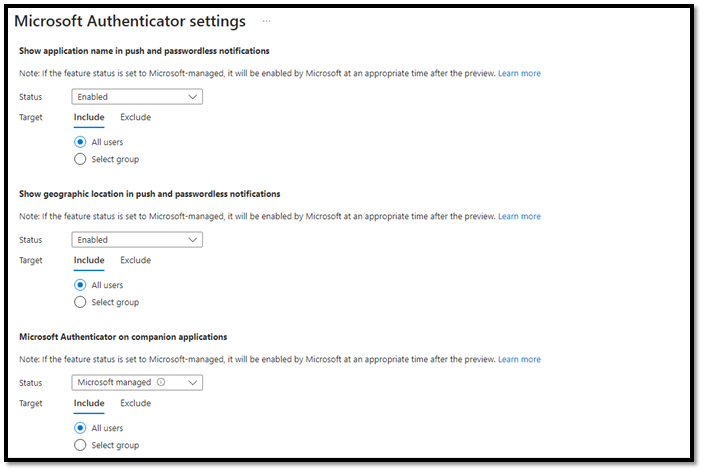
We highly recommend the following settings:
- Allow use of Microsoft Authenticator OTP -> No
- Require number matching for push notifications -> Enabled
- Show application name in push and Passwordless notifications -> Enabled
- Show geographic location in push and Passwordless notifications -> Enabled
Now that we are done with the above part, we will do the following:
Now that all legacy methods are disabled across legacy policies and Password Reset, we can complete the migration to Authentication Methods by switching to “Migration Complete”.
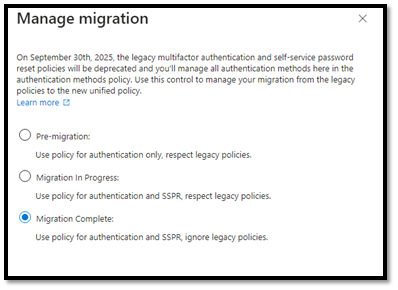
Once this is completed, we can be sure that Legacy policies are now ignored and most importantly, SMS is no longer an available option for MFA and Password Reset.
Microsoft Entra ID Bonus Features
Here are some additional features provided by Microsoft as part of Microsoft Entra ID (formerly Azure AD) to increase your security posture.
Conditional Access: Entra ID's Conditional Access feature allows you to set specific conditions that must be met before granting access to your digital identity. These conditions can include various factors such as time of access, location, device used, and user behavior. By defining these conditions, you can ensure that access to your Entra ID account is granted only under the circumstances you specify, adding an extra layer of security and control.
Passwordless Authentication: Passwordless authentication with Entra ID offers a secure, convenient, and compliant way to verify identity and access digital resources without relying on traditional passwords. Instead, users can leverage alternative authentication methods such as Microsoft Authenticator or using biometrics.
Single Sign-on: Simplify access to your software as a service (SaaS) apps, cloud apps, or on-premises apps from anywhere with single sign-on (SSO). With SSO, your teams can use just one set of credentials to conveniently access all their apps. No more memorizing multiple credentials or reusing passwords.
Identity Governance: Overall, Entra ID's entitlement management, lifecycle workflows, and privileged identity management capabilities provide organizations with comprehensive tools to manage identities, enforce access controls, and mitigate security risks across the enterprise. By automating identity management processes, enforcing least privilege access controls, and monitoring privileged activities, Entra ID helps organizations strengthen their security posture and achieve compliance with regulatory requirements.
Conclusion
In conclusion, we want to highlight that for Identity and Access Management, Authentication methods, and multi-factor authentication, you should not ignore the threats that may result from incorrect assumptions or opinions such as relying on SMS MFA authentication as a strong mechanism. These wrong assumptions may result in compromised security, reputation, and undermine customer trust. Furthermore, you should always think about investing in solutions that offer more than just basic necessities. To be effective in the cybersecurity landscape today you need to consider addressing the different threat scenarios more comprehensively to provide an integrated and holistic approach to security, and help you improve your risk management.
About Ravanty
We are a trusted Microsoft Solutions Partner and consultant, deeply rooted in the ecosystem since 2008. With our expertise, flexibility, and strong work ethic, we meet clients’ demands effectively. We guide you from objective translation to actionable results, customized to fit your unique business needs. Our unwavering commitment ensures your success within the Microsoft ecosystem.